This is the 2nd part of a 3 part series in protecting yourself from on-line and of-line scams. In part 1 I attempted to make you aware of some of the common ways in which a scammer operates. In this part of series, I will talk about ways you can avoid scams by being aware what to look for, and using technology to help you avoid scamms altogeather.
- The best security is awareness
- The psychology behind decision making
- Avoiding Scams
- Protecting yourself after the Scam
- Protect your on-line accounts
- Conclusion
- Updates: Spying on the Scammers Video
- Terms
Avoiding Scams
Search Results
Skipping Ads with an Adblocker
To avoid Ad listings in search results entirely, you can use a reputable Adblocker. Be aware that not all adblockers are created equal, some disguise themselves as adblockers, but instead deliver Ad’s to your computer. I use the Adblock Plus add-on/extension in Firefox and Google Chrome. It strips out Ad related content from many search engine results. This is the most effective way to protect you from malicious search results. Do not worry about losing any important results. Ad results are only companions to organic search results. If a result shows up in an Ad. I will show up in the search result if it is relevant to the search term. You might run into an occasion where you might need to whitelist a particular site from being blocked, and you can do that through the settings of the adblocker.
Avoiding Ads with Knowledge
If you do not want to use an Adblocker you can avoid malicious Ad results by knowing what to look for. The image below shows how Google, Yahoo, and Bing layout their Ad based search results. Headings highlighted in red contain the Ad listings.
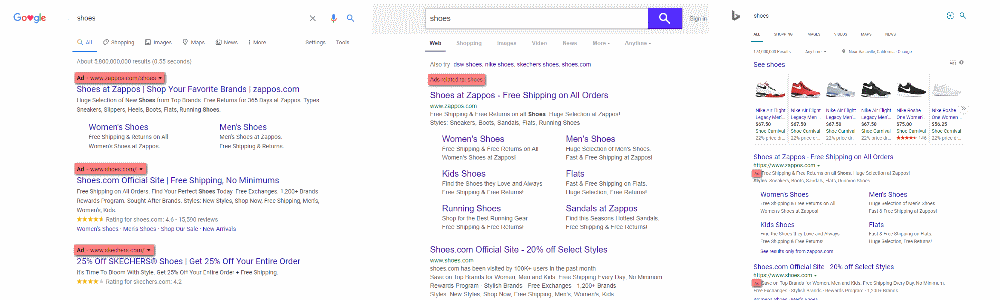
Search sites like those listed above have a platform for submitting Ads. This allows any “Joe” to create Ad campaigns that link directly to every day relevant search terms.
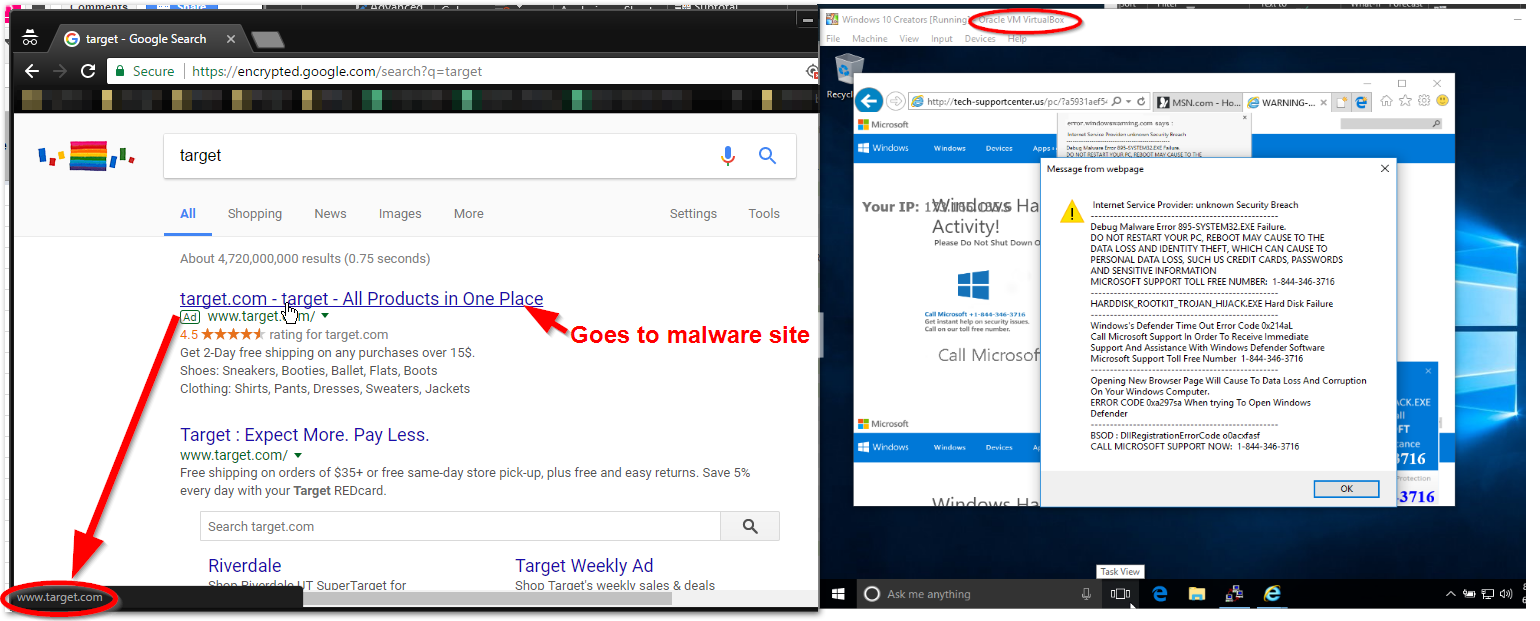
Google has a reporting system for malicious Ads, but by the time Google gets around to correcting the problem, you can be tricked into visiting a malicious site, and if you interact with that site, by then it’s usually too late. In some cases, your device can be compromised without any interaction.
Search results that are labeled “Ad” (See screen-shot above) can be redirected to an alternate site. This means that if you click on a link that you know is reputable, Google inserts itself in the middle and hijacks that link to send you to another location on the Internet.
Ultimately you want to avoid any of the search results that fall under the label “Advertisement”. Watch out for changes, many search engines change the way Ads are delivered on the search results page. Ad labeled search results usually appear at the top, a list of results can appear under one heading labeled “Advertisements”, or the label is tagged to each result itself.
Organic search results are ones that are not commercially supported and as such are less likely to have shenanigans attached to them.
Pop-up Warnings or Error Messages
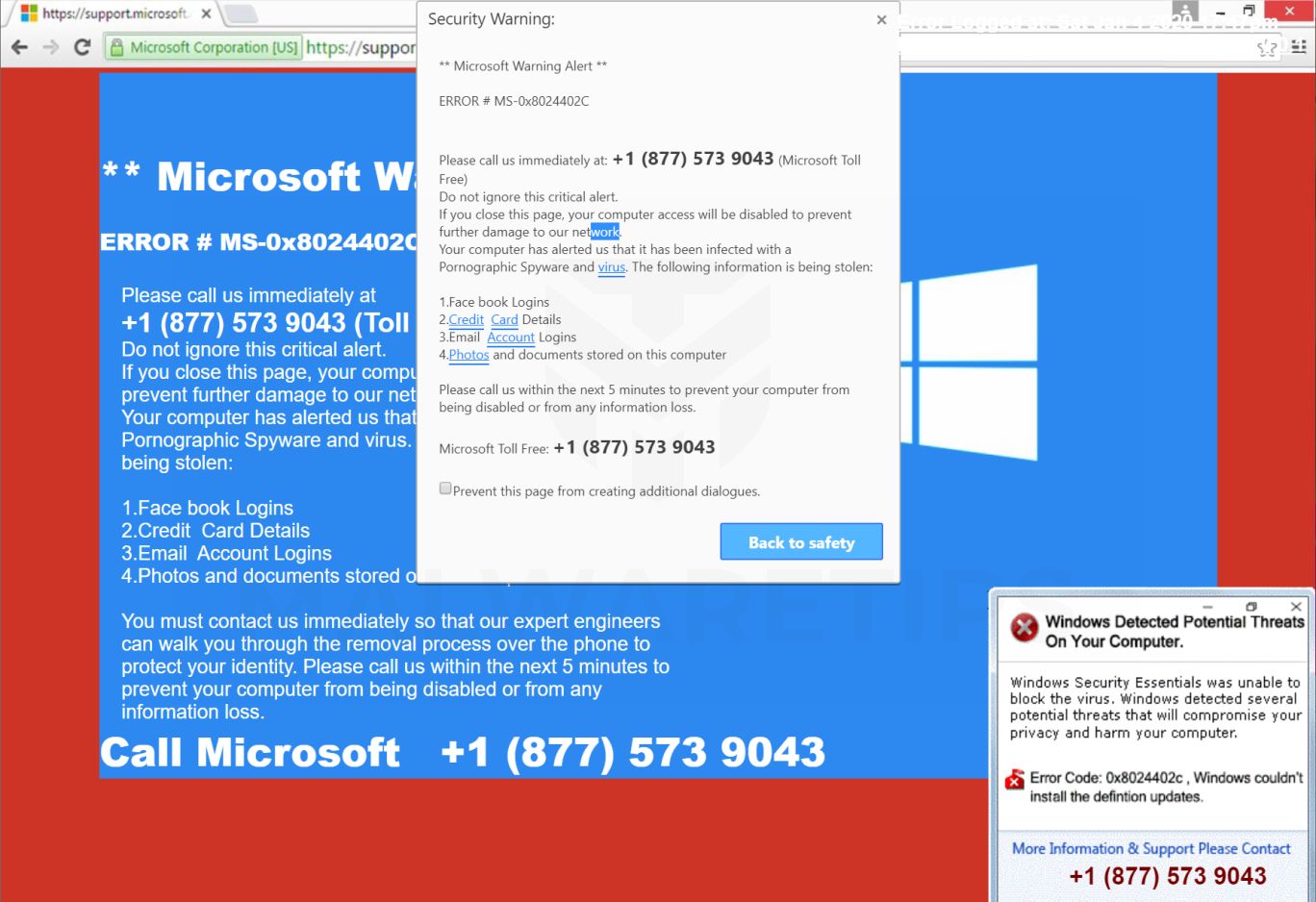
Within the scope of normal computer use, legitimate warnings or error messages never include phone numbers. Some specific business applications, like Quickbooks, are the exception.
If you receive an error message, or warning on your screen that you cannot get out of, do not interact with it in any way. Instead, you could immediately shutdown the computer by way of the power button. You can power down the computer by holding the power button down for 5-10 seconds and waiting until the screen goes black. Please note that there is a slight chance of data loss when you shutdown your computer in this fashion, but if you cannot get your computer to respond to a shutdown or restart command, or use the Task Manager to kill the task in question, it is my understanding these are the only options.
Call-based Scams

The trick to handling inbound call scams is to realize that, under most circumstances, obtaining computer support requires that you initiate the contact by your own means. When you receive an unsolicited call from an unknown agent, claiming to be from any legitimate establishment with the intent to offer you any kind of support, hang up. It’s that simple. Remember to maintain awareness of your decision-making psychology and don’t put yourself into situations that cause you to make snap decisions.
Do not make outbound calls from any error or warning message that appears on any of your devices. Remember the 3 indicators of a social engineering attack: Urgency, Pressure, and Illusion of Authority. If you need assistance, break away from the task at hand and ask a trusted person instead of blindly following a path that is laid out for you.
Email-based Scams
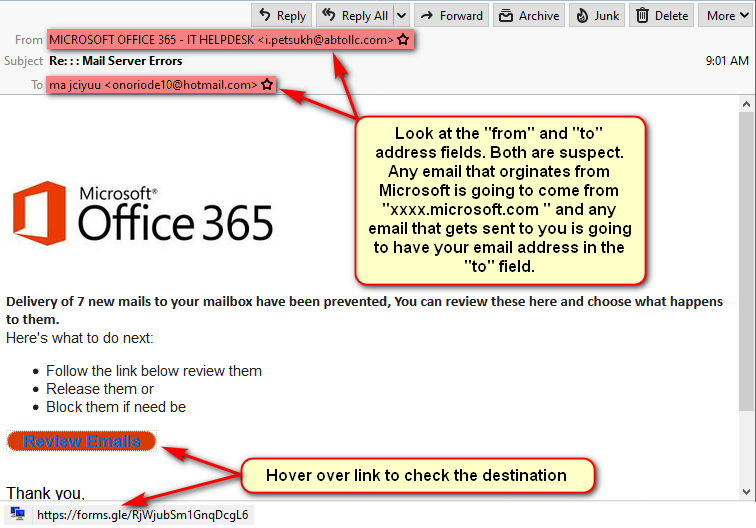
Making decisions on how to respond to emails that ask you to perform an action can be tricky. There are two categories of inbound emails from any provider:
- Legitimate requests to review information about your accounts or services.
- Illegitimate scams that attempt to portray themselves as legitimate requests.
When you receive an email asking you to perform an action, keep in mind the three basic qualifiers of legitimacy:
- Who is the email sender? Are you receiving an email from Microsoft asking you about your email? Do you even have an email with Microsoft? Find out who your mail provider is. If it’s not Microsoft, delete the message. If you do have an Email with Microsoft move on to the next step.
- What is the message asking me to do? Depending on the request, you can sometimes tell that the message is suspect by the way the message is crafted, or by the nature of the request. If the email states that an account you own is on hold because of a billing problem and the message requests that you click on a link to remedy the problem, instead, open up your web browser and visit the site by using web browser1 to confirm that problem exists.
- Where will I land if I act? Without clicking on any links in the email, move your mouse over the link and look at the destination URL. If it doesn’t contain a recognizable location, you know you got a problem.
How to respond to calls for help from family, friends, or colleagues.
In some cases, you may encounter a situation, usually by email or social networking, where a contact looks to be someone close to you, who reaches out to you for help in some way. Many scammers steal the identity of a person to target the victims network of contacts. Once the identity has been compromised is some way, the attacker will trying to appeal to individuals in the victims network with a request of good will by crafting a message of help. The message will probably look like a request for money. The contact might mention a travel situation where the contact is in a bind and needs help. Then there might be a link to send that person money.
Another regular method of attack is to trick an individual from victims network into giving away personal details, like bank account information, or any site where your credit card is stored by convincing the target to click on a link that takes the victim to a page that looks like a legitimate website, but instead is a malicious site used to steal account credentials.
The best way to deal with these situations is to try to reach out using outside methods. Call the contact and verify via voice that the message is legit. If you cant reach the person, call or text a close friend and see if they know anything about the situation.
Conclusion
My goal in this part of the series was to show you some ways in which a scammer might trick you into giving away personally identifying information with some ways you can avoid this. In part 3 I will discuss ways to protect yourself after you have become a victim of a scam.
If you have any questions about this publication, or you would like help with your computer’s security, contact me. I can assess your protection, and offer suggestions to improve your online safeguards.
Part 3..>
- A Web Browser is software that allow you to interface with sites on the world wide web. Google Chrome, Firefox and Internet Explorer are a few popular examples. These applications make it so you can visit sites on the web. ^